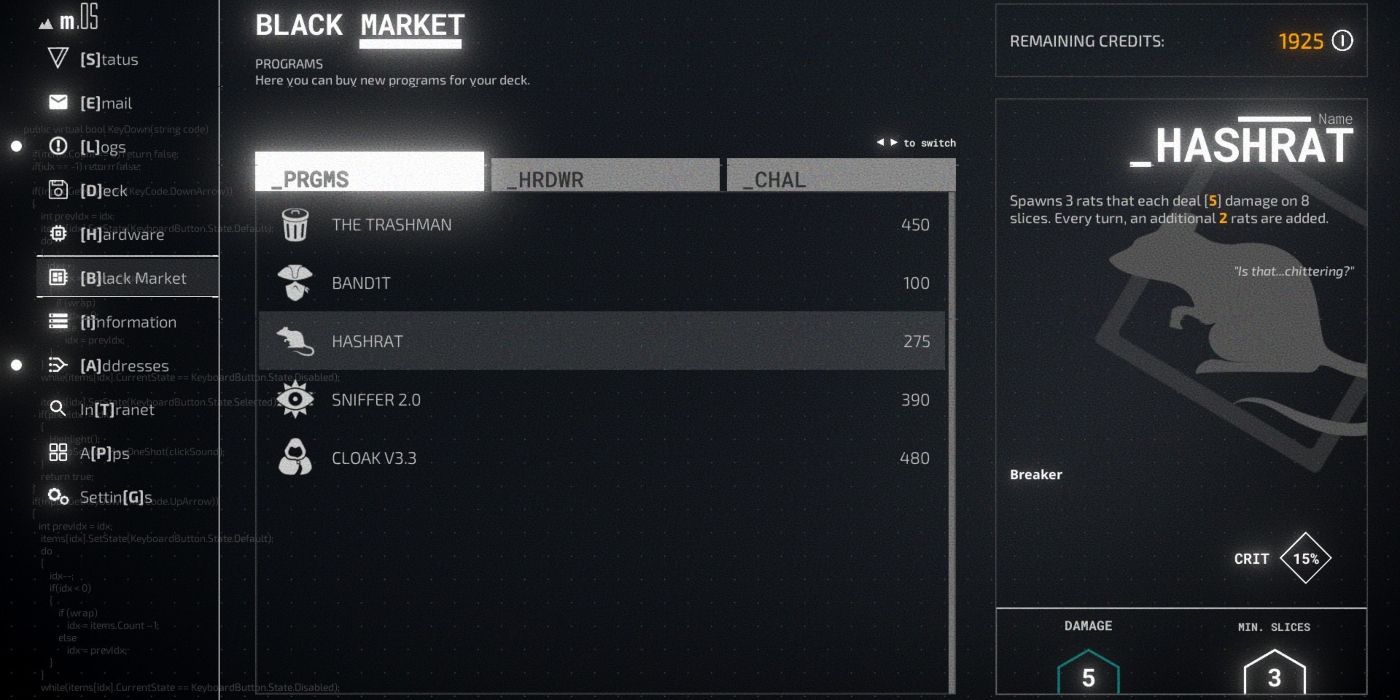
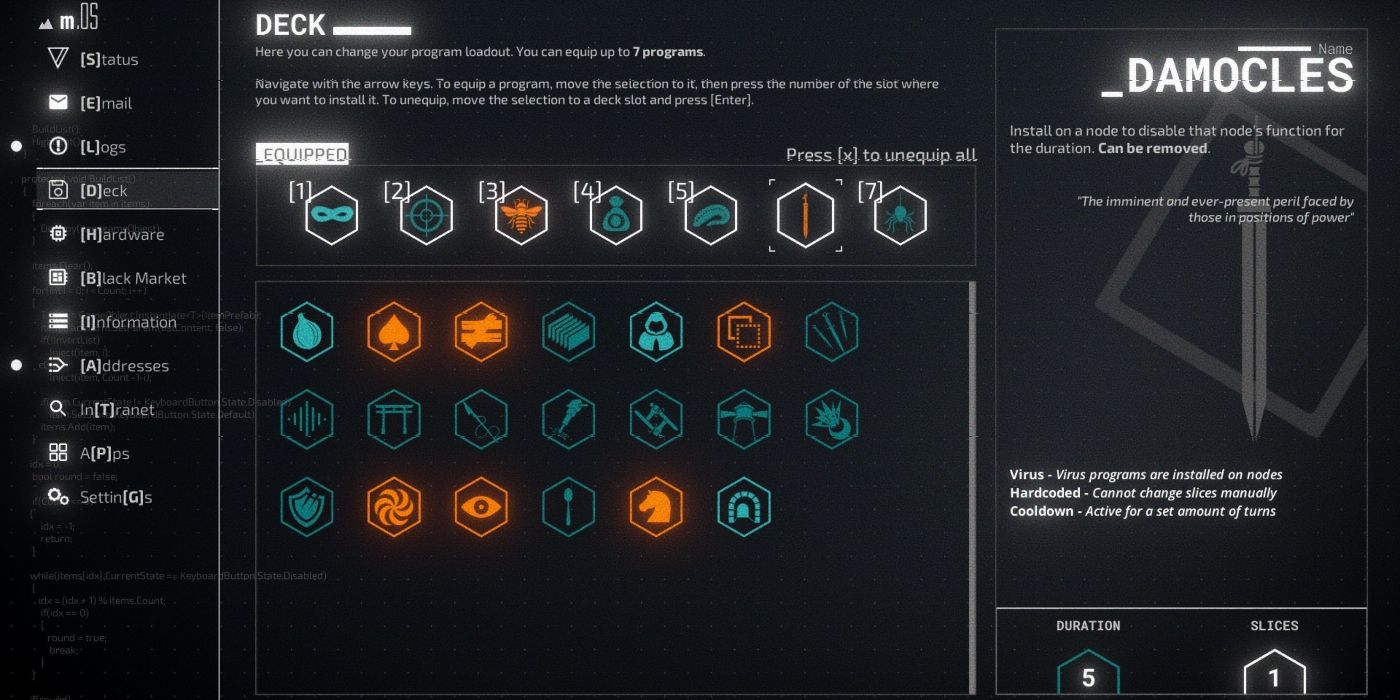
A narrative hacking simulator, LuGus Studios’ Midnight Protocol puts the player into the driver’s seat and outfits them with a customizable array of programs and hardware. Earning black, gray, or white hats, or spending hard-stolen credits are the means through which players will acquire and purchase new tools to place into their deck. Credits are a limited resource, and deciding which is the most optimal to purchase, and which to then bring on any given mission, is a part of the game’s strategy.
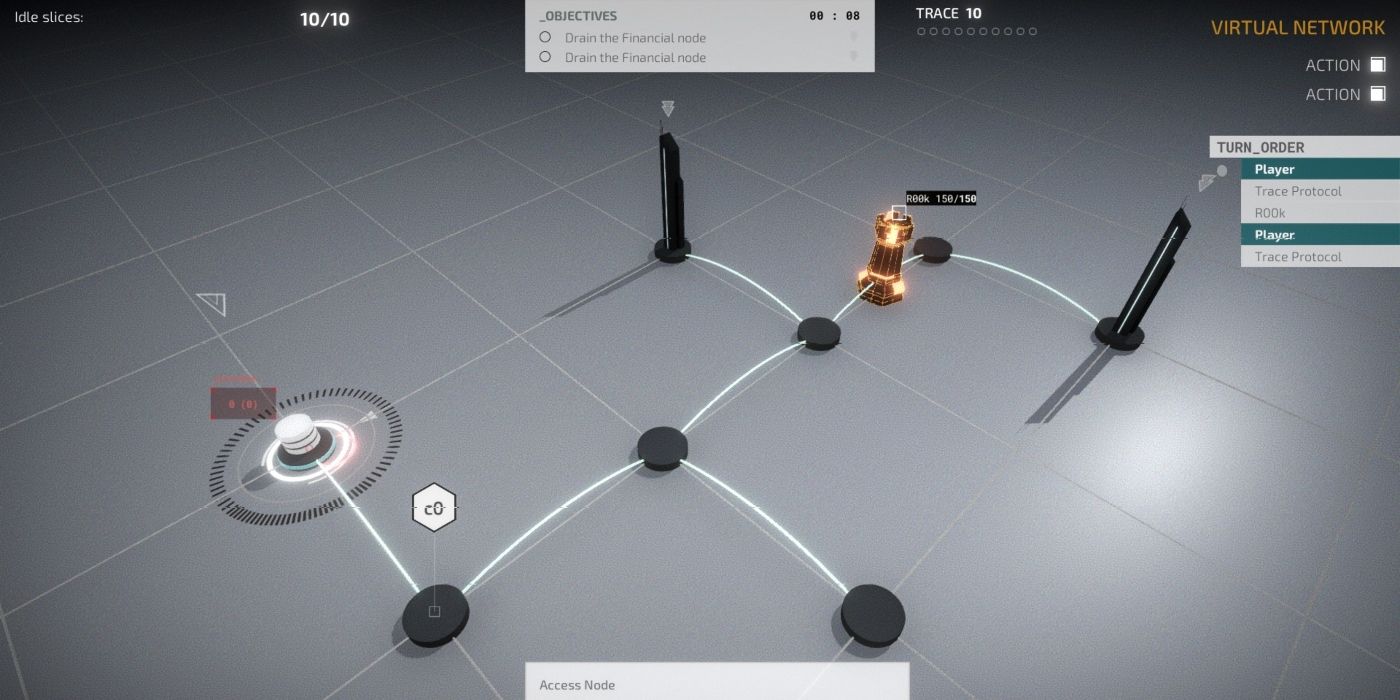
Developed by LuGus Studios and published by Iceberg Interactive, Midnight Protocol’s design is a turn-based RPG. One plays as a hacker, typing commands to eliminate dangerous ICE, cloak themselves from the growing trace bar, or threaten to release compromising photos in order to blackmail a desperate husband. These Mass Effect-style life or death decisions will determine the morality and alignment of Data, the player character, and will result in not only different endings, but what kinds of programs or hardware are made available to her.
These choices are presented in most missions and side quests throughout the game, and they directly impact the kind of hacking style Data opts for. At one point there’s literally an option to get an NPC arrested and empty their character’s bank accounts or leave their kids’ college tuition intact and instead reroute them back to safety. Undertaking more criminal side quests or operating on blackmail from a shadowy branch of government will result in Black Hat points and make available more aggressive breakers.
Succeeding in Midnight Protocol Is All About Building The Best Deck
Expediting police investigations, rebooting offline satellites, or hacking datapads and computers to relieve those targeted by blackmail in Midnight Protocol instead garners White Hat points. Reaching new tiers of White Hat reputation means more defensive capabilities, like enhanced stealth programs or hardware to extend the trace bar. Gray Hat reputation is gained free of moral choices, and simply represents that Data is growing into a more capable and renowned hacker.
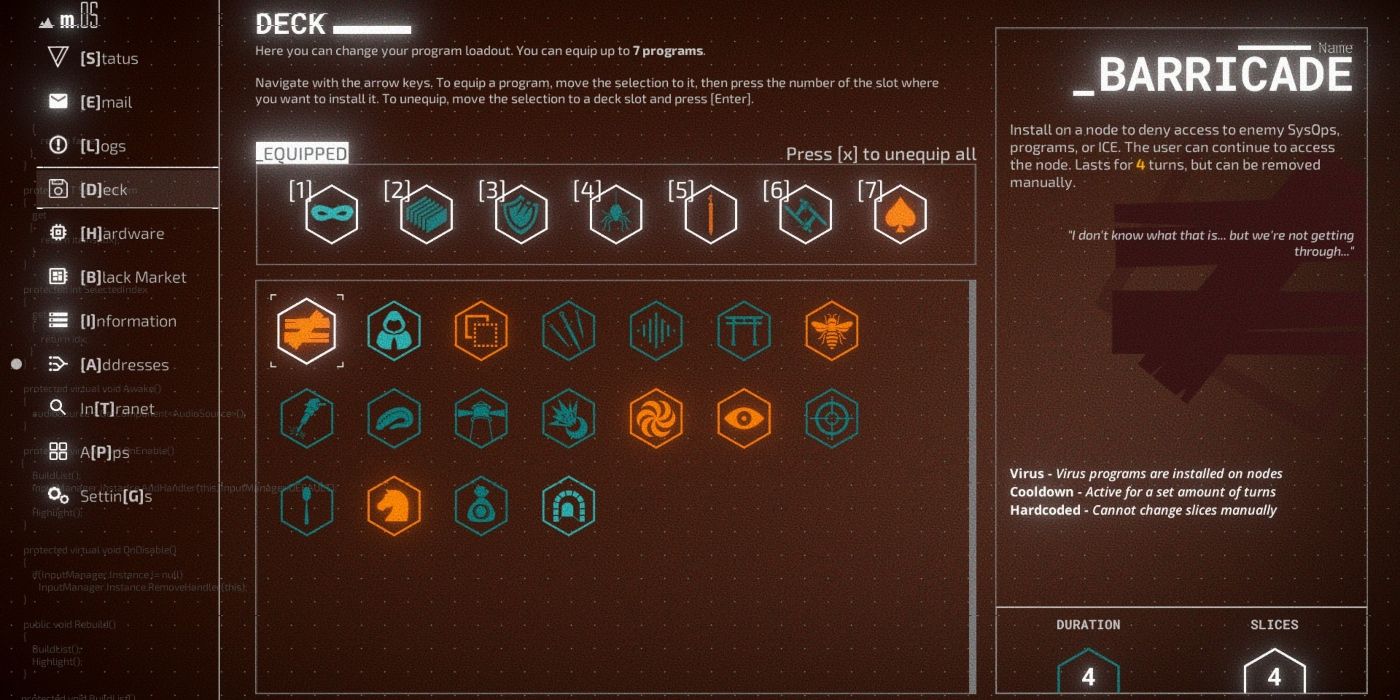
Data’s chosen permutation of programs to take on a mission is referred to as her ‘deck.’ Cracking a digital safe or extracting classified data requires careful planning and might even be impossible without equipping the right programs before a mission. It’s always a smart choice to check the requirements and expected obstacles for a mission before embarking on it.
If there are Encryption nodes present in Midnight Protocol, the Spoon program is going to be a huge help, even if it’s not typically one of the better programs available. There’s also a strategy to solving the game’s mystery by bringing along specific programs like Trojan. Trojan’s slow installation, large resource drain, and meager 10% increase make it less effective than some of the later programs in the game, but it’s still encouraged to bring it along on certain missions for plot reasons.
There are several programs that, no matter the mission, will frequently end up in Data’s deck. One such program is Mask, unlocked via White Hat reputation. This stealth program costs a hefty four slices, but grants Data 90% protection each turn against being traced. This is especially useful early on in the game. The downside of Mask, however, is that it’s automatically removed any time the player spends both of their turn actions moving.
Midnight Protocol’s Best Deck Builds Can Be Angled Or Well-Rounded
Every program in Midnight Protocol has its pros and cons, and that’s where optimizing a deck comes in. For example, since Mask discourages movement, it doesn’t work well with Echo, a breaker program that only deals damage when the player switches to a new node. This encourages changing loadouts, like in the metagame, Warzone. Hive, since the slower mission pace means Data can instead spend that turn action planting the breaker on new vacant nodes. This boosts Hive’s power each time, and on larger networks, it’s possible to bore through even higher-level ICE in just a couple of turns.
Further along in the game, more advanced programs become available for purchase. The breakers become both more destructive and more specific to respective ICE. Viruses and support programs offer more powerful unique abilities, but will require more slices to initiate. This allows players to either build a more rounded deck in which programs cover each other’s weaknesses, or instead have an angled deck in which advantageous traits are stacked together.
This latter option could mean a quick noisy brute-force approach in Midnight Protocol, like the DDOS attacks that took down World of Warcraft's servers back in 2021. This strategy is valid, but leaves Data extra vulnerable to trace, or it could mean an extra safe and slow, methodical approach. When dealing with sturdier ICE, a smaller trace bar or an aggressive SysOp, this can be just as risky. If a firewall is blocking progression, sometimes it’s better to smash through it and suffer the trace consequences rather than be a sitting duck for a SysOp.
An example of a rounded deck might comprise Cloak, Trojan, and Echo. Cloak’s 75% trace protection isn’t as reliable as the 90% from Mask, but it has no movement penalties. That means Echo can fire twice per turn without any drawbacks. Echo is one of the weaker breakers, however, and that’s when Trojan comes in. Typically a more irrational choice, Trojan becomes a benefit by boosting both Echo and Cloak by 10%. This increases Echo’s damage per hit as well as raises Cloak’s protection up to a maximum of 85%.
How To Build Midnight Protocol’s Best Decks
A more angled deck in Midnight Protocol, by contrast, would focus on stacking breakers and rapid movement. King, Ace, and Jackhammer can get the job done quickly, but noisily, and in the end, requires just as many slices as the former deck build. In this example, King is an area of effect attack that only triggers when a program is removed. Ace makes it so removing programs doesn’t take a turn action. Finally, Jackhammer is a strong, but loud, breaker that deals especially high damage to wall ICE.
Removing Jackhammer will cause King to attack, but since Ace is enabled it won’t cost a turn action. You can spend that turn freed up action re-initiating Jackhammer, effectively attacking the same ICE multiple times in a single turn. For efficient thieves, however, the build should almost always include Buffer.
Buffer shrugs off one trace attempt for every slice that’s currently unoccupied. This can be used to mitigate the amount of passive trace accrued when going loud. It can also be used as a makeshift stealth program like Mask or Cloak, with both 100% accuracy and no movement penalty. There is a catch with Buffer, however: Once the program’s time runs out there’s a Cooldown period that takes up as many slices for as many turns as Buffer was engaged.
A good Midnight Protocol deck should also have some means of scouting. Tripping an ICE is never pleasant in a hacking video game, particularly when the trace bar is short or there’s a SysOp on the network. Sniffer is the first option available, and it’s a solid choice on most missions. Having Echo S hardware installed can highlight which connections are harboring ICE, but without Sniffer they can’t actually be revealed and dealt with.
The Best Midnight Protocol Decks Have Varied Programs
Spider, and later Bandit, can sub in for Sniffer in Midnight Protocol. Depending on the other programs in the deck, and what kind of hardware is selected, these could be better or worse choices. Spider is handy since it costs very few slices and both detects and reveals ICE every turn. When it comes to crafting an optimal system for the game, however, it should be noted that Spider’s movements are random. Bandit can highlight ICE on multiple connections at once, but provides no way to reveal it. It also costs one more slice than Sniffer, but only occupies them for one turn.
Hardware is the final factor to consider when building a deck, as the right components can strengthen breakers, lengthen the trace bar, or even open more available slots for the deck altogether. This offers new options for deck permutations dramatically, facilitating creative combinations and clever strategies.
More slots available in Midnight Protocol also frees up space to bring more mission-specific programs like Spoon, Leech, or Troll Toll. The complexity of Midnight Protocol’s RPG system makes the game both replayable and challenging, and encourages multiple solutions to each puzzle. Once the player figures out which combinations work best together, it’s still up to them to decide the best approach to any given mission.
Midnight Protocol is available on PC, MacOS, and Linux.